Buffer Overflows: Why Old Bugs Still Matter
After 25 years in information security, I've seen my fair share of vulnerabilities come and go. There's one classic that never seems to fade away: the humble buffer overflow. From my early days writing C/C++ code and hunting down memory leaks, to performing white hat hacking and teaching security training with sample overflow exploits, I've witnessed firsthand how this seemingly simple memory management issue can cause major problems. Buffer overflows aren't just academic exercises or relics from the 1990s; they're still very much alive in today's high-performance systems, and they're particularly relevant when building software that need to handle millions of events per second reliably.
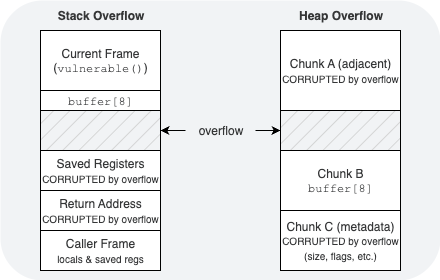
A buffer overflow happens when a program writes more data into memory than the allocated space allows. Instead of stopping, the excess data spills into adjacent memory. That corruption can cause crashes, data leaks, or — in the most dangerous cases — remote code execution.
