User Guide
Account Settings
You can view and edit current user’s account settings (Display Name, Email address and password) via this view.
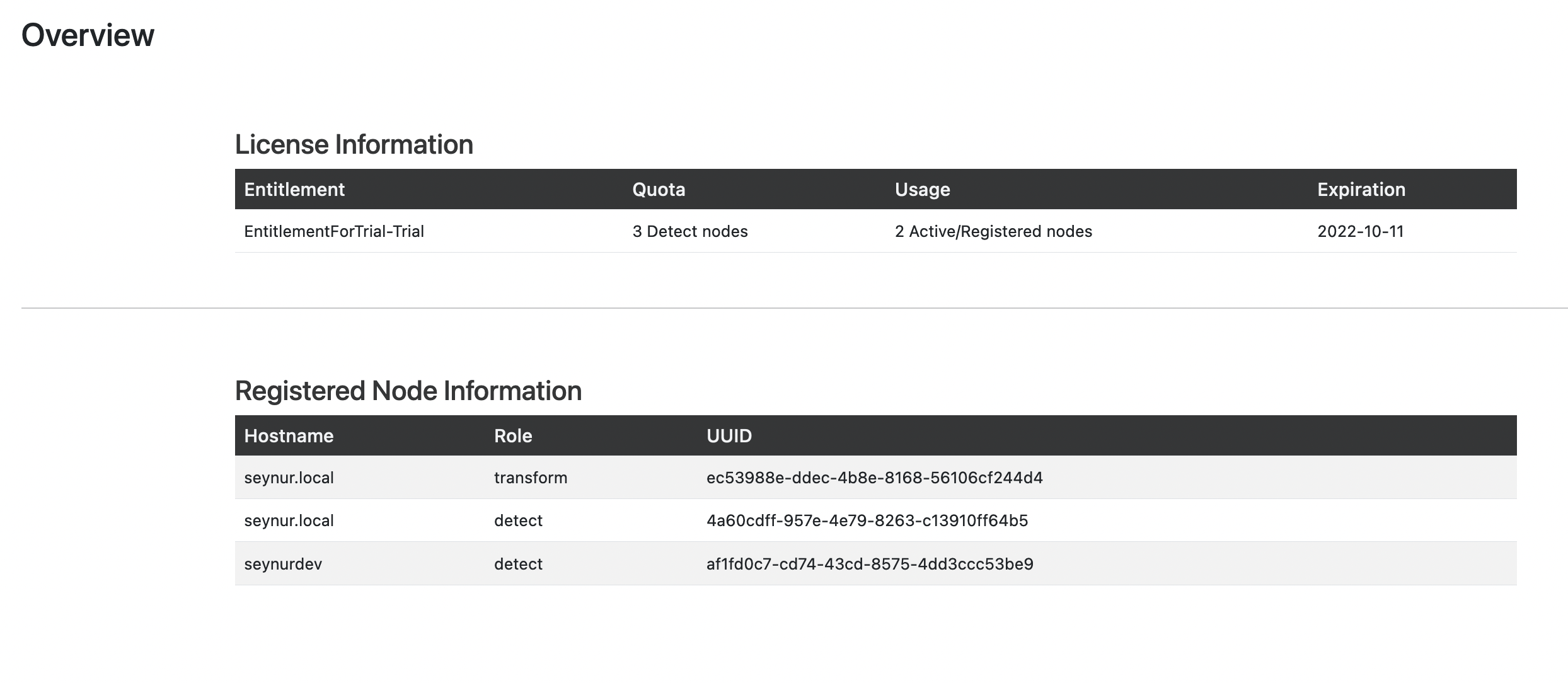
About Overview
Overview provides information regarding license information and registered nodes. Note that licensing quota is based on number of Detect nodes with an expiration date.
Registered Node Information table provides details on actively running PADAS instances (other than this manager).
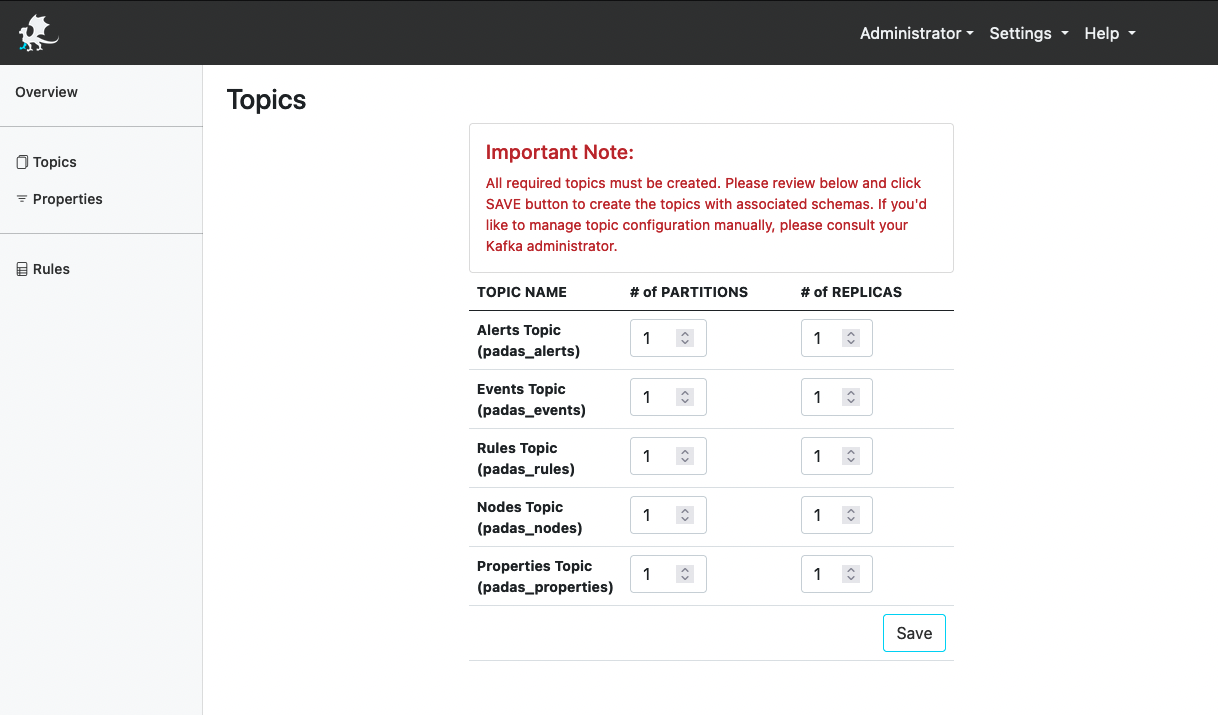
Topics
Upon initial login, PADAS Manager checks whether all required topics are created and available. If any one of the required topics is missing, you’ll be redirected to Topics view in order to view and update existing settings. This is a simple interface to create required Kafka topics through PADAS Manager interface.
Important Note: Number of partitions can NOT be changed/updated once a topic is created. This value depends on your data volume and scalability requirements. If you need to change/update this value for any reason, the topic will need to be deleted and created again with new values. For more information regarding topics, please refer to Topic Properties
If you need more control over topic creation, please consult your Kafka/PADAS administrator; you can also refer to Confluent Documentation.
Properties
Properties view provides configuration entries for Detect and Transform Engine components. You can click Edit button to enter in edit mode and make changes. Following table provides information on the form fields.
NOTE: You can upload (click Upload Properties from File button) and/or download (click Download Properties button) properties as a file. A sample properties file for Winlogbeat transformations can be found here: Winlogbeat Sysmon and Security
NOTE: You can click Add New Transformation button to add new input topics for analysis. The input topic must exist prior to starting PADAS Transform Engine.
NOTE: After any configuration changes, you will need to restart the corresponding component(s) (i.e. Detect and/or Transform Engine(s)). PADAS instances read and load the configuration upon starting.
Detect Engine Properties
| Display Name | Property Name | Required | Default Value | Description |
|---|---|---|---|---|
| Omit Raw Data | alerts.topic.omit.rawdata |
yes | false |
Define whether to omit raw data when generating PADAS Alerts. |
| Omit Json Data | alerts.topic.omit.jsondata |
yes | false |
Define whether to omit JSON data when generating PADAS Alerts. |
| Event Datetime Pattern | event.datetime.pattern |
yes | yyyy-MM-dd'T'HH:mm:ss.SSSZ |
Timestamp pattern to extract from Padas Events. It is recommended use the default value. |
Transform Engine Properties (for each Input Topic)
N starts with 0 and incremented by 1 (e.g. 0,1,2,3, etc.)
| Display Name | Property Name | Required | Default Value | Description |
|---|---|---|---|---|
| Topic Name | input.topic.N.name |
yes | Define whether to omit raw data when generating PADAS Alerts. | |
| Enabled | input.topic.N.enabled |
no | true |
Defines whether this transformation is enabled or not |
| Raw Data Field | input.topic.N.rawdata.field |
no | event value | Defines the extracted field that has the raw event data. If undefined, all event value is used. |
| Omit Raw Data | input.topic.N.omit.rawdata |
no | false |
Defines whether to omit raw data when populating PADAS Events |
| Extraction | input.topic.N.extraction |
no | json |
Defines how to extract fields from input topic. Available values are json and regex. If regex is specified, Regex definition is used for extraction. |
| Regex | input.topic.N.regex |
no | Defines a regular expression on how to extract fields from the topic's value. Applicable only when extraction is set to regex.
For regular expressions, only named-capturing groups are allowed currently for field extractions. Please refer to Java Regex Pattern for details.
Example for apache: ^(?<host>[^ ]*) [^ ]* (?<user>[^ ]*) \[(?<time>[^\]]*)\] "(?<method>\S+)(?: +(?<path>[^\"]*?)(?: +\S*)?)?" (?<code>[^ ]*) (?<size>[^ ]*)(?: "(?<referer>[^\"]*)" "(?<agent>[^\"]*)")?$
|
|
| Timestamp Field | input.topic.N.timestamp.field |
no | Defines the extracted field to be used as the timestamp of the event. If left empty or unspecified, current time is used. | |
| Timestamp Pattern | input.topic.N.timestamp.pattern |
no | yyyy-MM-dd'T'HH:mm:ss.SSSZ |
Defines the pattern for timestamp field, if specified. |
| Host Name | input.topic.N.host.name |
no | current hostname | Defines the hostname for this event (static). This setting is only applicable if host.field is NOT specified. |
| Host Field | input.topic.N.host.field |
no | Defines the field to be used as hostname for this event (dynamic). This setting overwrites host.name |
|
| Source Name | input.topic.N.source.name |
no | input topic name | Defines the source for this event (static). This setting is only applicable if source.field is NOT specified. |
| Source Field | input.topic.N.source.field |
no | Defines the field to be used as source for this event (dynamic). This setting overwrites source.name |
|
| Datamodel Name | input.topic.N.datamodel.name |
no | input topic name | Defines the datamodel for this event (static). This setting is only applicable if datamodel.field is NOT specified. |
| Datamodel Field | input.topic.N.datamodel.field |
no | Defines the field to be used as datamodel for this event (dynamic). This setting overwrites datamodel.name |
|
| Event src Value | input.topic.N.src.value |
no | Defines the source host/IP address for this event (static). This setting is only applicable if src.field is NOT specified. |
|
| Event src Field | input.topic.N.src.field |
no | Defines the field to be used as source host/IP address for this event (dynamic). This setting overwrites src.value |
|
| Event dest Value | input.topic.N.dest.value |
no | Defines the destination host/IP address for this event (static). This setting is only applicable if dest.field is NOT specified. |
|
| Event dest Field | input.topic.N.dest.field |
no | Defines the field to be used as destination host/IP address for this event (dynamic). This setting overwrites dest.value |
|
| Event user Value | input.topic.N.user.value |
no | Defines the user associated with this event (static). This setting is only applicable if user.field is NOT specified. |
|
| Event user Field | input.topic.N.user.field |
no | Defines the field to be used as the user identifer for this event (dynamic). This setting overwrites user.value |
Properties View Sample

Rules
Rules view provides configuration entries for Detect Engine rules that are applicable to various data models (as specified in transformations or padas_events topic). Relevant schema for PADAS topics can be found here.
NOTE: You can upload (click Upload Rules from File button) and/or download (click Download Rules button) rules as a JSON file. An out-of-the-box JSON rule file is provided for Winlogbeat according to MITRE ATT&CK framework and can be found here: padasRules.json
NOTE: You can click Add New Rule button to add new detection rule.
NOTE: Any change in detection rules is effective immediately (updates padas_rules topic) and does NOT require any restart/refresh.
Detection Rules Configuration
| Display Name | JSON Field Name | Type | Required | Default Value | Description |
|---|---|---|---|---|---|
| Rule Name | name |
string |
yes | Rule name(e.g. Attack Detection - Successful Local Account Login). | |
| Rule Description | description |
string |
yes | A brief description for this rule. (e.g. The successful use of Pass The Hash for lateral movement between workstations). | |
| PDL Query | pdl |
string |
yes | PDL Query to match the event. (e.g. event_id=4624 AND event_data.TargetUserName!='ANONYMOUS LOGON'). Go to PDL Reference for details. |
|
| Enabled | enabled |
boolean |
yes | true |
Defines whether this rule is enabled and active. |
| Datamodel List | datamodelList |
string array |
yes | Comma separated list of Datamodels where this rule will be applicable to. These MUST match the datamodels in Padas Events (padas_events) topic, probably populated via Padas Transformation(s). (e.g. sysmon, wineventlog). |
|
| Additional/Optional Configuation | |||||
| Omit Raw Data from alerts | omitRawdataFromAlerts |
boolean |
yes | false |
Defines whether to omit raw data from generated alert(s), i.e. padas_alerts topic. |
| Omit JSON Data from alerts | omitJsondataFromAlerts |
boolean |
yes | false |
Defines whether to omit JSON data from generated alert(s), i.e. padas_alerts topic. |
| References | references |
string array |
no | Comma separated list of references for this rule. | |
| Platform | platforms |
string |
no | Applicable platform(s) for this rule. (e.g. Windows) |
|
| Domain | domain |
string |
yes | mitre_attack |
Applicable domain for this rule. (e.g. mitre_attack) |
| Severity | severity |
string |
no | String representing severity of this detection (e.g. medium) |
|
| Custom Annotations | customAnnotations |
string array |
no | Please enter any custom annotations (e.g. CIS20, KillChain, NIST, etc.) as a comma separated list pertinent to this rule |
|
| MITRE ATT&CK Annotations | |||||
| (sub)Technique ID List | mitreAnnotations |
string array |
no | MITRE ATT&CK Technique and Subtechnique IDs as a comma separated list. (e.g. T1550, T1550.001, T1550.002). |
|
| Analytic Type | analyticType |
string |
no | Applicable analytic type for this rule according to MITRE Cyber Analytics Repository (e.g. Situational Awareness) |
|
| Datamodel References | datamodelReferences[] PadasDatamodelReference |
string |
no | List of datamodel reference triplets (object|action|field) separated by commas. (e.g. process|create|command_line, process|create|exe) |
|
Rules View Sample
